Security monitoring and analytics
TV piracy keeps growing and becoming more industrialized
OTT streaming has revolutionized the way content is delivered to consumers on various devices, including mobile, tablets, TV dongles, set-top boxes, and TVs. Unlike traditional TV networks, which have a physical delivery perimeter, with OTT over the internet and interconnected cloud deployments, content can move from one global location to another in a matter of milliseconds. However, this positive evolution has also made illegitimate access to content and services industrialized and easier than ever for pirates.
In 2019, Parks Associates estimated that video piracy cost pay-TV and OTT providers $9.1 billion in lost revenue. That number is projected to increase to $12.5 billion by 2024, representing a 38% growth rate.
Although Digital Rights Management (DRM) has always been the primary layer of content protection in OTT and sufficient to enforce access rights, it has weakened over the years. Some design weaknesses combined with the lack of control over implementation on devices have led to hacks resulting in content leaks and service frauds in streaming services.
Even if governance around DRM implementation becomes strict and systematic, an OTT service cannot ignore the thousands of security-weak device models currently used by consumers. These devices are fully owned by consumers and cutting them off from the OTT service would trigger subscriber churn. When DRM is compromised and content keys are leaked, a pirate service can connect to a service provider’s content delivery networks (CDNs) to fetch content, descramble, and consume. This type of industrialized or automated pirate flow is increasing pressure on CDNs and forcing them to rethink their security design. While CDNs have always favoured performance and cost efficiency over security, weakened DRMs have made security equally important for service providers to avoid serious complaints from content owners or bear additional costs on CDNs due to pirate traffic.
To add some control over content delivery, many service providers have patched their CDNs with techniques such as the use of authentication tokens with some level of binding, however pirates have become smarter, employing various fraudulent techniques to continue to steal content.
Even in a world where DRM remains secure, one can still steal content using techniques like HDMI ripping. Once downloaded and uncompressed in an application or device, the stolen content can be re-encoded, recompressed, and sent to the cloud to be redistributed to millions of devices worldwide. While this issue has existed for years, the difference nowadays is the availability of cheaper video capture ripping devices, democratization of the cloud, automated video management workflows, and high internet bandwidth, making such piracy widely exploited.
Credential sharing, also known as subscription sharing or co-owning, is another growing piracy technique. With content owners offering direct-to-consumer services with unique and interesting content, in addition to the well-established OTT services like Netflix, Disney+, Apple TV, and Amazon Prime, consumers are incentivized to share their credentials to access the maximum content without stacking up subscription fees. While sharing within the perimeter of a given family may be tolerated to some extent, the reality is that this is happening on a much wider level, and many commercial pirates have found ways to make money by offering cheaper and more attractive bundles than legitimate services, such as diivii.com and accountbot.io.
According to Parks Associates, 27% of U.S. broadband households currently engage in some form of piracy or service fraud like credential sharing. This poses a significant threat to the revenue streams of legitimate streaming services.
By looking at the offers proposed by credential sharing or pooling websites, a simple calculation can demonstrate the potential revenue loss for service providers. For example, if 10% of a 1 million subscriber base is using a pirate service rather than paying $10/month, this will result in a $1 million monthly loss in revenue. This does not include the incremental CDN costs incurred by video service providers due to pirate services routing their traffic via service provider CDNs, which can run into petabytes per month.
To combat this type of advanced piracy, service providers must look at utilizing machine learning algorithms. Overall, the rise of credential sharing highlights the need for service providers to be vigilant and proactive in their efforts to protect their content and revenue streams.

ASP – Security Monitoring and Analytics
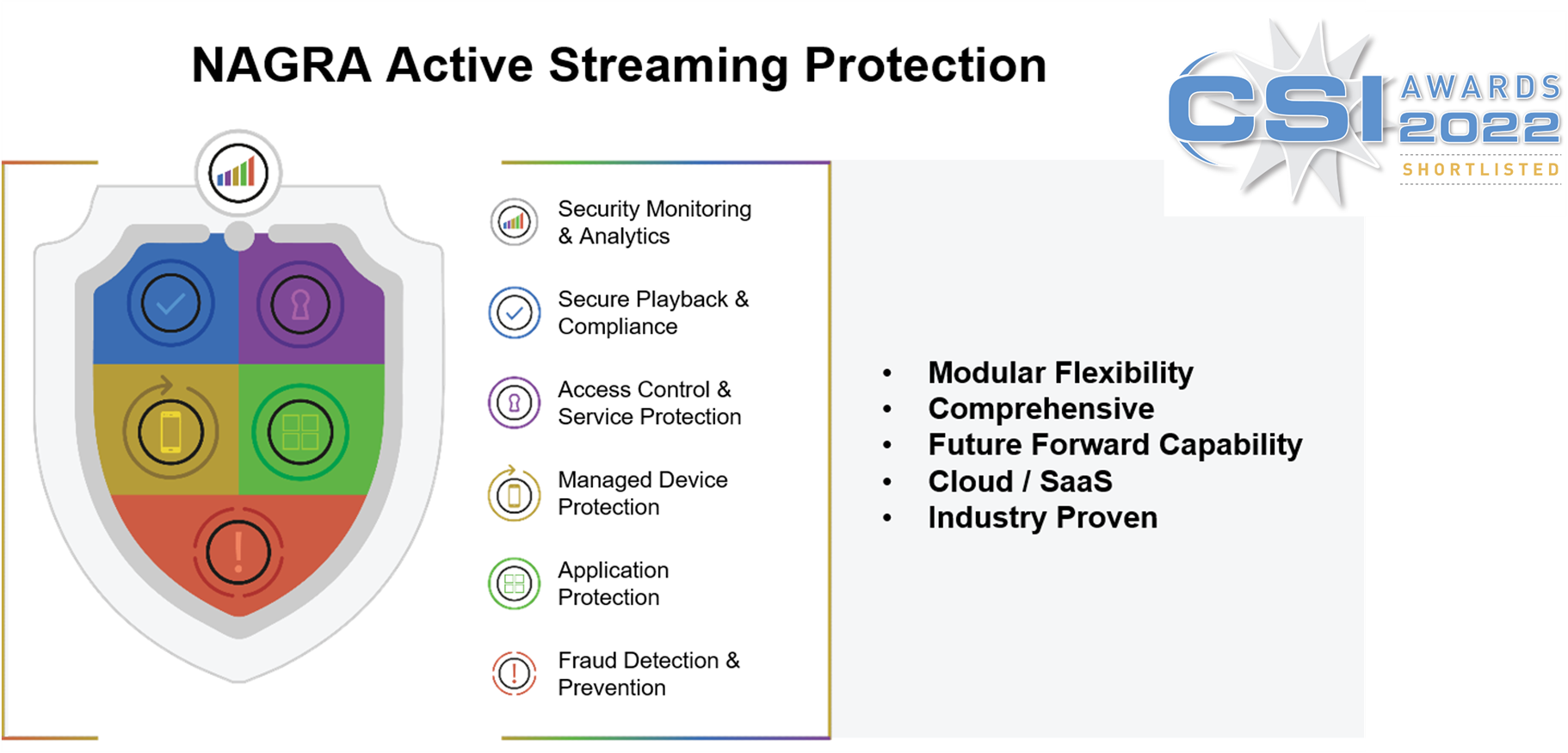
NAGRA has developed a comprehensive and holistic streaming security framework called Active Streaming Protection (ASP), to help TV service providers address piracy challenges on OTT streaming. ASP enables OTT streaming providers to manage security risks related to both content and service piracy while driving advanced business models with confidence.
ASP comprises a set of technologies and services to address threats related to content and service piracy. Each pillar of ASP addresses a specific group of threats. These pillars work together to provide a comprehensive, holistic, and sustainable approach to streaming protection.
With ASP, service providers can benefit from advanced features like session tracking, piracy monitoring and analytics, device-based forensic watermarking, and multi-DRM management to secure their content and services against piracy threats. ASP provides a one-stop solution to streaming security challenges, enabling service providers to focus on delivering high-quality content and user experience to their customers.
Overall, ASP is a powerful tool for TV service providers to address piracy challenges in the OTT streaming world and secure their revenue streams and brand reputation in a highly competitive market.
The Security Monitoring and Analytics pillar is a key component of ASP, taking a data-driven approach to help streaming service providers monitor and detect content leaks and service frauds happening on their platforms. While other pillars like Multi-DRM, Secure Session Management, Device Authentication, Watermarking, and Application Hardening try to bring proactive security, there are always pirates finding ways to outsmart these measures. Thus, the Security Monitoring and Analytics pillar remains the ultimate tool for guerrilla fighting against streaming piracy.
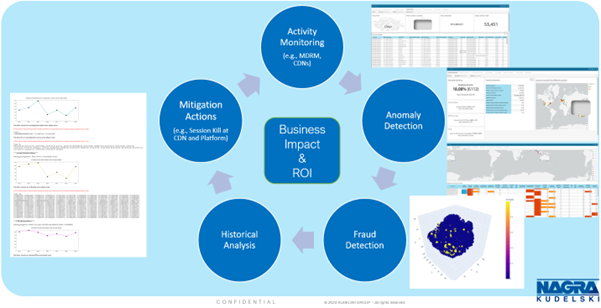
The data-driven ASP Security Monitoring & Analytics intelligence layer crunches logs from security-related workflows, from DRM to CDN, to achieve various objectives, including providing advanced intelligent security dashboards for analyzing consumer activity, detecting suspicious subscriber accounts based on a multitude of indicators and features, detecting specific frauds such as credential sharing, account rotation, and other forms of fraud, conducting historical behavior analysis, and improved anomaly detection using artificial intelligence and machine learning (AI/ML).
By analyzing data from different sources, the Security Monitoring and Analytics pillar enables service providers to identify potential security breaches and take proactive measures to prevent piracy, content leaks, and service frauds. This helps them to protect their content and services against unauthorized access and ensure that their revenue streams remain secure.
Overall, the Security Monitoring and Analytics pillar is a crucial component of ASP, enabling service providers to monitor and detect piracy threats, detect frauds, and optimize their content delivery processes to provide their subscribers with a high-quality viewing experience.
The ASP Security Monitoring & Analytics pillar has been successful in detecting between 10% and 15% of subscriber accounts as "suspicious" to date. With this information, service providers can zoom in on the detected accounts and learn more about their usage patterns, including the number of devices the account is using, what the device models are, how frequently they are consuming content, what types of content are consumed, and details about their related streaming sessions.
By correlating this data with CDN data, service providers can gain insights into TV platform activity and CDNs. Post detection, service providers can take multiple mitigation actions, ranging from suspending fraudulent subscriber accounts and revoking access to suspicious devices to killing streaming sessions and proposing new commercial offers to convert illicit device users into paying subscribers.
An example of this approach is Netflix, which has recently started enforcing usage rules in regions such as Latin America to ensure that an account is not shared beyond a certain family circle perimeter. If the family members sharing the account are not from the same household, the related account is detected as suspicious. Once detected, the main account holder is asked to add the account-sharing users formally to their subscription for an additional cost.
Overall, ASP Security Monitoring & Analytics provide service providers with valuable insights and tools to combat piracy, protect their content and services, and optimize their business models.
Monitoring
The ASP Security Monitoring & Analytics solution is a comprehensive system designed to provide service providers with enhanced security measures to protect their streaming services from content leaks and service fraud. One of the key features of this solution is the monitoring component, which enables service providers to visualize application and device activities at various levels. This monitoring feature allows service providers to aggregate data related to account, device, and content, giving them a detailed overview of the activities occurring within their consumers. By using this aggregated data, service providers can quickly make informed decisions about what is happening in the field and how their business is evolving over time.
This comprehensive overview allows service providers to track and analyze user activity, identify patterns and trends, and take proactive measures to improve the overall service. By using this data, content providers can optimize their services, enhance their content offerings, and tailor their marketing strategies to reach their target audience more effectively. Overall, this solution provides service providers with valuable insights into their consumers' content consumption patterns from trustworthy data sources, helping them to make informed decisions that drive business success.
Account-level view
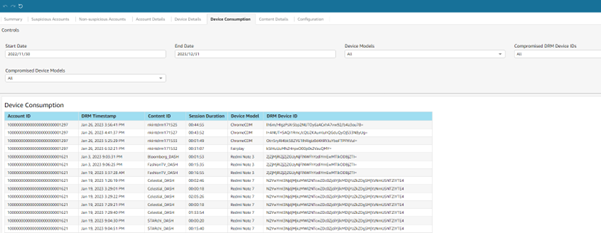
This page provides service providers with a detailed list of all content playback requests, along with relevant information about each playback session. Users can easily visualize which subscriber consumed what content, when the playback occurred, for how long, and on which device. Additionally, users can see what Digital Rights Management (DRM) was used to decrypt the content and the physical location of the device used to connect to the system.
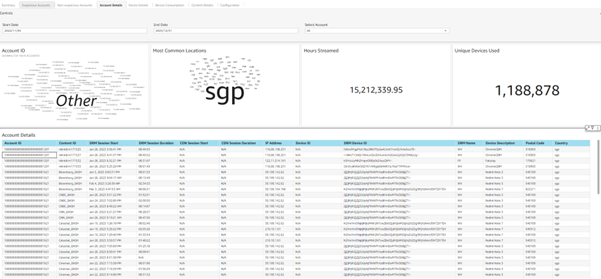
This account level view also offers a timeline view of key metrics to facilitate quick visualization for service providers. These metrics include the number of unique countries from which devices are connecting, the number of different postal codes from where streaming sessions have been requested, the number of hours of content played, and the number of unique devices. By offering this timeline view, service providers can easily track and analyze how these metrics change over time, enabling them to identify patterns and trends.
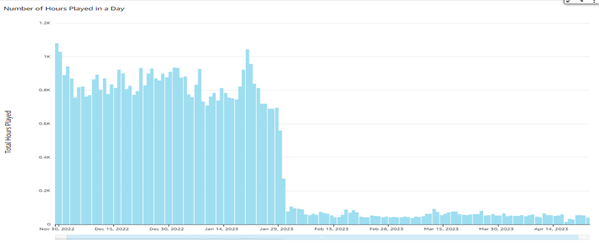
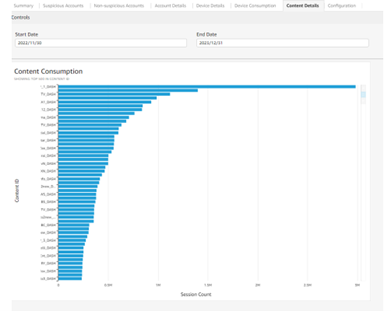
Content-level view
Like the account-level view, ASP Security Monitoring & Analytics also provides an aggregated view at the content level. This feature enables service providers to quickly see which content is popular and which is not. By visualizing this data, service providers can identify popular content and optimize their content offerings to meet their audience's needs. Additionally, like all other views, this content-level view can be further customized by adding filters to fine-tune the research. This customization feature provides service providers with the flexibility to view and analyze the data in a way that is most relevant to their business needs.
| |
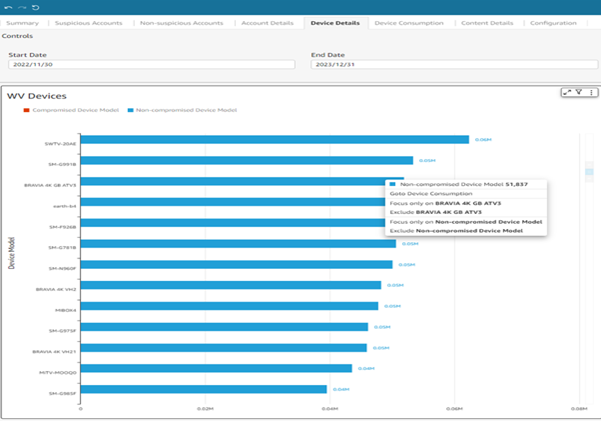
Device-level view
The device view in ASP Security Monitoring & Analytics provides two key visualizations. First, it shows the different device models used by consumers and the related number of transactions that occurred during the defined period. Second, it allows service providers to zoom into transactions made by a given device model.
In the world of Digital Rights Management (DRM), where poor implementation of DRM into devices is one of the major causes of piracy, this view is crucial for assessing the level of activity originating from compromised device models. DRM providers often maintain a list of compromised device IDs and device model IDs. By using this view, service providers can easily check whether their subscribers are using those compromised devices. If so, they can blacklist them to reduce piracy exposure.
Overall, the device view feature in ASP Security Monitoring & Analytics provides valuable device insights to service providers, helping them to detect and mitigate potential security threats and reduce piracy risks.
Configuration
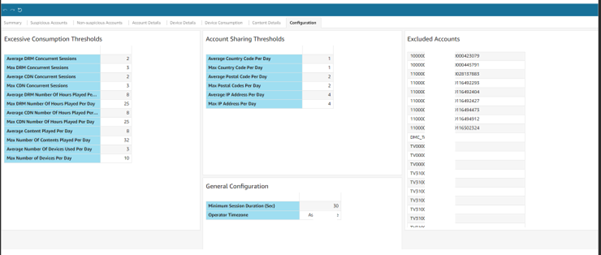
ASP Security Monitoring & Analytics allows a certain level of service provider-specific configurations, mainly in the form of threshold values that the analytics algorithms should consider. By allowing service providers to configure these threshold values, the solution can be tailored to meet the unique context of each service provider. Additionally, these threshold values can be adjusted over time to adapt to changes in the business and consumption patterns.
Analytics-Light
Summary view
This page in ASP Security Monitoring & Analytics provides a summary of the aggregated metrics and detected anomalies. The aggregated metrics include data related to account, device, and content levels, providing service providers with valuable insights into subscriber behavior and content consumption patterns. This data is presented in a clear and concise manner, allowing service providers to quickly assess the performance of their OTT streaming services and identify areas for improvement.
In addition to the aggregated metrics, the page also highlights a summary of detected anomalies, such as suspicious subscriber accounts that are sharing credentials or contributing to other forms of content leaks and service frauds.
By providing a comprehensive overview of the key metrics and anomalies, this page enables service providers to make informed decisions that drive business success.
- The period of analytics in ASP Security Monitoring & Analytics is defined by selecting a start date and an end date. This enables service providers to focus their analysis on a specific time period and gain insights into subscriber behavior.
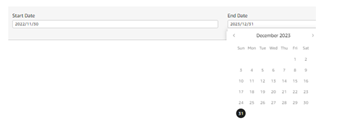
- Aggregated key metrics for a selected period
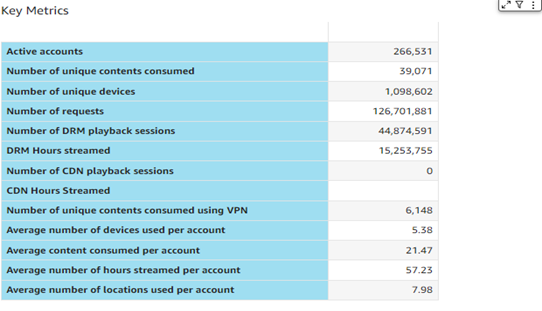
- Map showing where the consumers / devices are connecting from; in green: non-suspicious, in red: suspicious (see the section for more details)
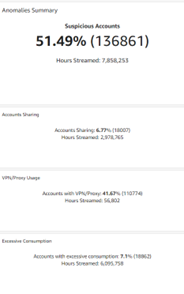
- Summary of the anomalies detected. For an account (subscriber ID) to be tagged as “suspicious”, it must be caught by one of the three algorithms: account sharing, excessive onsumption, and use of VPN/proxy.
- The example below shows that in total 54.49% of the accounts are caught by one of the three algorithms with details on algorithm-specific contributions.
Suspicious view
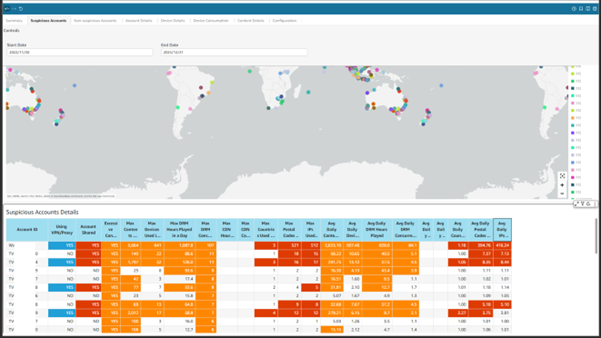
This is the view where multiple indicators are assembled and analyzed to detect whether a subscriber is either sharing accounts, consuming content excessively, or using a VPN/proxy, and is a valuable tool for service providers. The threshold value for these indicators is configurable per service provider, enabling them to customize the detection based on their specific needs and preferences.
This type of "suspicious" activity detection based on human explainable indicators remains a valuable first level of detection before applying advanced fraud detection schemes as part of the Analytics-Advanced bundle. NAGRA strongly believes that this type of human intelligence-based first-level anomaly detection, coupled with a strong TV piracy knowledge, is essential before thinking about any advanced models.
By focusing on these human explainable indicators, service providers can gain valuable insights into subscriber behavior and detect suspicious activity that may be indicative of piracy. This already enables them to take proactive measures to prevent piracy and protect their content and services from unauthorized access. Overall, this view is a valuable first level of piracy detection for service providers looking to optimize their OTT streaming services and combat piracy threats.
Analytics-Advanced
Analytics-Advanced is an extension to the Analytics-Light bundle in ASP Security Monitoring & Analytics, which provides enhanced anomaly detection and fraud detection capabilities. This advanced bundle includes historical views, enabling service providers to monitor repetitive patterns over weeks and identify trends in subscriber behavior and piracy threats.
Moreover, Analytics-Advanced allows service providers to confront the piracy view from DRM with the view from CDN. The view from DRM shows what should be happening, whereas the CDN view shows what has actually happened. By comparing these views, service providers can identify any deviation or gap between them, which can then be further analyzed to find advanced content leak and service fraud patterns.
The Analytics-Advanced bundle employs advanced machine learning algorithms and artificial intelligence models to detect even the most complex piracy threats, enabling service providers to take proactive measures to prevent piracy and protect their revenue streams. Overall, this advanced bundle is a valuable tool for service providers looking to optimize their OTT streaming services and combat piracy threats at a deeper level.
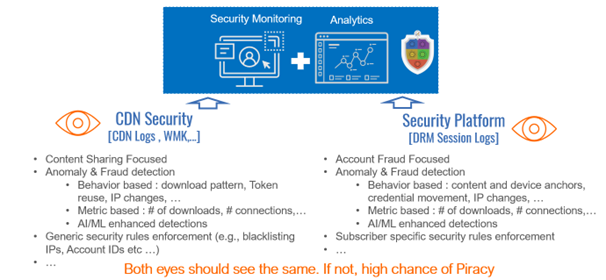
NAGRA applies multiple algorithms from behavior-based to metric-based to AI/ML-based on both the CDN and DRM sides to detect content leaks and service fraud. These algorithms are equally fine-tuned between live and VOD content. NAGRA has identified unique piracy patterns inlLive TV that differ from those found in VOD, and the algorithms used to detect these patterns are tailored to each content type.
Behavior-based algorithms analyze subscriber behavior and activity, looking for patterns and anomalies that may be indicative of piracy. Metric-based algorithms monitor key performance indicators, such as the number of unique devices, IP addresses, and geolocation data, to detect anomalies that may be indicative of piracy. AI/ML-based algorithms analyze large data sets to identify complex patterns and trends that may be difficult to detect using traditional methods.
By stacking these multiple algorithms, NAGRA is able to detect content leaks and service fraud more accurately and efficiently, enabling service providers to take proactive measures to prevent piracy and protect their revenue streams. Overall, NAGRA's comprehensive approach to piracy detection and prevention is a valuable tool for service providers looking to optimize their OTT streaming services and combat piracy threats.
Further Information
If you’d like to learn more, experience NAGRA Active Streaming Protection, or discuss how NAGRA can do an initial security sweep across your ecosystem to show how your service is affected by piracy, please drop us an email at dtv@nagra.com. We look forward to continuing the conversation with you. You can also find a wealth of resources such as this short video on our website.